Theory and Practice of Asymmetrical Communication Endpoints (ACE's)
By
Heinrich T. Feuerbach, February 2019
email: info@feuerbach.info
Copyright: Author, but free for Wikipedia. See below statement related to the GPL.
Introduction
This article first describes the theoretical background of asymmetrical communication in networks such as the Internet and its advantages in the area of data security. This is followed in a second section by the description of one of the possible implementations of an asymmetrical computer system using conventional means (Ethernet, PCs), currently only in the German version of this page. This serves as practical proof of the correctness of the theory, a PoC (Proof of concept). Delimitation: "asymmetrical communication in networks" does not mean the different bandwidth in internet connections for upload and download. Rather, it is a matter of building the sender and receiver of a client computer separately in order to obtain certain physical security advantages. Nor is it about communication via simple data diodes, which e.g. through optical connections ensure one-sided communication. If to stay with the comparison of the data diodes, one would have to speak rather of a "bridge rectifier", because the ACE supports both communication directions.
Important information regarding the licensing of the here directly and for download offered information and files: since August 1st, 2020, all, both hardware and software, is under the GPL v.3.
(see full text on https://www.gnu.org/licenses/gpl-3.0.html.) Every other license terms, wherever mentioned, are no longer valid.
This short overview of a new type of endpoints for networks like the Internet shows how to avoid these scenarios. It is related to End-user-Computers, so the mass-market, typical Client-Computers. An “Asymmetrical Communication Endpoint” or ACE provides the technical platform to solve these issues for all use-cases. An ACE describes a Computer-System which consists not of just one single Computer but of two. This pair of Computers is presented to the user as a single one Computer, so the “Duality” is transparent to the user.
One of both Computers is physically able only to send data into the Internet, while the other one is physically able to only receive data from the Internet. Given that, the term of “Asymmetry” is here related to the functions of “transmitting/sending” and “receiving” of data.
Such a system is safe against intruders from the networks to which it is willingly connected, like the Internet, in a physical manner.
As being physically safe, this high level of security is independent of Software-Updates. All attacks via the eg. Internet against such Computer System is ineffective, if the attacks are initiated and performed through the Internet, so fully “from outside”.Neither espionage nor manipulation of data or sabotage can be successful against an ACE.
Only precondition is having the data on both Computers of the ACE, or only on the transmitter because of the fact that the data on the receiver is further in reach of attackers. I call the side represented by transmitter and receiver as “Green” because having here a level of security for the data hosted on an ACE in the middle between a symmetrically with the Internet connected Computer (“Red”) and a fully isolated or “air-gapped” Computer ("Blue"). For the transmitter itself I use the color “Green”, for the receiver the color “Yellow”. These colors again showing their individual level of data security with the transmitter providing more security for the hosted data then the receiver. So Green and Yellow building together the “green side” of the ACE.
An ACE can be universally used for networked and non-networked programs.
Before explaining the ACE more in detail, here an ex-course into a classification of the different security levels.
Introduction of a Classification of all Types of Attacks against Computers
To describe the level of security for the data in a Computer System and to be at same time able to compare the levels of security of different systems, we need first to be able to classify somehow all the possible attacks on them.
In other words, every known but also every possible future type of attack must have its place in the classification.
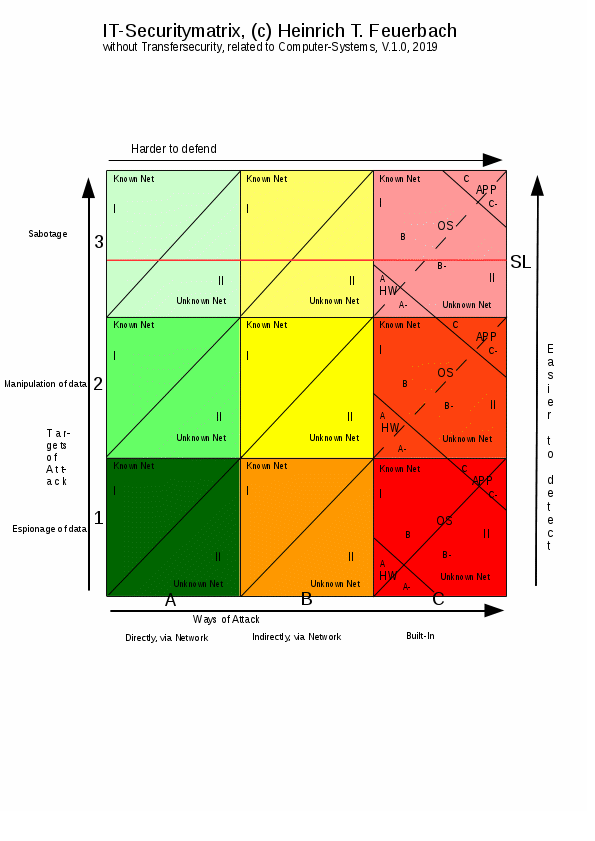
For this, I set up a matrix, consisting of 9 main fields as 3x3. The resulting two dimensions are the “targets” and the “path’s” of attacks. Targets may be the read-out of data in a given Computer-system, the manipulation of data in a given Computer-system (writing) and the sabotage against the data or the system at all.
Path’s may be the direct network attacks, the indirect network attacks and the built-in attacks.
Given that, every possible attack is a combination of these two dimensions.
These resulting 9 fields are then each split into two, for known and unknown networks. A known network is a network which is known to the owner and user of the Computer-system, whilst an unknown network is not. An unknown network is for example a cell-phone which is connected to one of the LAN-Computers for the purpose of loading its battery. As the cable used here has also wires for data transport via USB and the cell-phone being connected to the Internet, this way the user creates, unwillingly or not, another network connection, here into the Internet. Through this connection, which is unknown to the owner of the Computer, may now the system be attacked, going simply around the possibly expensive firewall.
This is just one of many examples for unknown networks. There are found such like communication via ultra sounds from TV sets to cell (smart-) phones, LEDs on Computers and network equipment sending out data and many other ways to “extract” data from systems or manipulate data without the knowledge of the owner of that system. Such unknown networks are even used to bridge the air gap of isolated Computer-systems, monitoring or controlling them, going around all other security measures.
Coming back to the matrix of 9 fields, there is a classification of all attacks in visible to the user and invisible to the user needed. For example sabotage attacks are often soon visible to the users of the attacked systems, however not always. All depends also on the intention of the attackers. There are attacks aiming at sabotage being so long as possible not detected by the users of the target like in case of the attacks on the Uranium enrichment systems of Iran via “bridging the air gap” methods.
Other sabotage attacks don’t try to hide, they even aim at being visible, like DDoS, de-facing of Websites etc.
Given these differences in the visibility of attacks, there is a “visibility line” in the most upper row of targets, the sabotage row in the matrix. This horizontal line, however, is not always flat, it may, depending on the attack, be changing its position and form like a wave.
The defender will always try to block all 9 fields completely, whilst an attacker would try to attack where it is the easiest.
Individual fields may be defended absolutely with physical measure, or just partwise, so in percentiles.
An absolute coverage
of a field means that an attacker can never succeed. This is only
possible if a demonstrable, such as physical, protection takes
place. All other measures can only be hedged to an estimated
percentage.
The ACE
absolutely covers the areas B3 (transmitter) and (A3 + C1)
(receiver).
In this case, the area A3 is covered for the
receiver due to an upstream firewall ("FW").

Fig.1, Attack- or security matrix of computer systems
Explanations to
Fig.1:
The attack matrix consists of 9 main fields with 2
dimensions, the attack paths and the attack targets. The fields are
divided again, mainly into known and unknown nets.
The coloring of
the graphic has nothing to do with the color scheme of the nets above
and is independent of it. The color scheme of the graphic I have
chosen so that this color corresponds to the potential danger of each
field: green less dangerous, red most dangerous and hard to ward off.
The brightness of the colors, which increases in the diagram at the
top, indicates the visibility of an attack on the associated
field: the lighter the color, the sooner an attack is visible to the
user.
The example case
of a known network is when someone connects a computer, whether
symmetrical or asymmetrical, to the Internet in a controlled manner.
This connection to the Internet is then desired and can be removed by
the user at any time.
The case of an unknown network is when
someone has a connection unknown to him and
therefore not desired by the owner of the computer or network, e.g.
into the Internet, for
example, via a mobile phone with GPRS data transfer option, which
connects to the computer, the associated LAN, or a network device,
thereby opening an unknown network connection, drain on the data or
can also flow out.
This
inflow or outflow of data is then beyond the control of the user or
owner of the computer system or network.
Even the unshielded
computer monitor is part of it, if it sends the screen data
electromagnetically into the surrounding area, as well as the
keyboard cable, which is not shielded, network cables, which are not
shielded, etc.
A further subdivision takes
place in column "C" into fields for HW, operating system
and application programs. This corresponds to the various areas in
which a malware, regardless of which destination, in the computer
already from production or even after delivery, etc. may be
installed, so even without any network connection can already be
present.
Finally, there is another subdivision in Above and Below
the Visibility Line, "SL". Attacks that are directly
visible or tangible to the user are above the SL, all attacks that
are not visible or not immediately visible are below the SL. The SL
therefore corresponds to a "waterline": the further below
the waterline, the harder the attack is to be
detected. Unfortunately, only sabotage attacks
are in many cases directly and immediately recognizable by the user
of the system.
With
the names of Roman numerals (I and II), letters and minus signs, each
individual field can be clearly named and distinguished. In addition,
the feature "above" or "below" the SL can be
used.
If you want to name an area of several main fields, you name
the right-uppermost
field of the area. For individual fields, they are named as "Field
Xn".
Multiple areas of fields can also be connected by a plus
sign, such as (A3 + C1).
The common area in the attack matrix, which can be covered by both the transmitter and the receiver by the ACE only due to asymmetry, is the "L" of A3 and B1. All other fields can cover either only the transmitter (up to B3) or only the receiver (up to C1), thus the asymmetry alone gives as measure "only" a cover A3 and B1, the A3 safety of an upstream FW included - for the green side so green and yellow together.
The dividing lines in
the fields C2 and C3 are dashed, since here the meaning of the
network connections is limited: An attack on C2 can also without
completely network come into effect, since this means data
manipulation by built-in malware. If this is already on a given
computer system, a network is no longer needed to take
effect; however, if it is not already on a given computer system,
then again a network connection is needed to spread to other
computers. Otherwise it can only work locally. The same applies to
implemented or built-in sabotage software, field C3.
Now every
single attack can be clearly assigned to one of the fields.
The
defender should try to cover all fields, especially the ones
below.
The further to the right a field lies, the harder it is to
cover. The further down, the harder it is to detect an attack and
thus prevent it; therefore, the most problematic field for the
defender is C1.
Examples
of attacks on the individual fields:
Column A, direct attacks via
networks: these are only possible on an endpoint in known networks if
no firewall (FW) has been installed upstream. Unknown networks will
rarely have an FW upstream, so these are the more likely routes of
attack.
This can e.g. via an unknown WLAN access, via a USB cable
to one of the computers located in the LAN, etc. Even unknown
communication via ultrasound as with various mobile apps often as
Trojan available, come here in question.
There are many
possibilities for unknown nets, every espionage bug, which has been
fixed under a conference table, thus represents an unknown net. Also
infrared, the electrical
net, etc. can come into question for the attack. Through various
shielding measures, these can be prevented, via e.g. sensors
it can be recognized.
In
column "B" we are already dealing with attacks that are
much harder to combat because they come from the inside, indirectly
via the network. Examples are the Trojans that one "captures"
via email attachments. After such an attachment has been opened by
the recipient, the Trojan (field B1) collects data such as passwords,
emails, etc. in plain text unnoticed by the person being attacked.
Then he sends this in case of symmetrical networking in the Internet
to the attacker. Another example is the remote control: the Trojan
contains a server with which the attacker can watch the screen
content live at any time without the user noticing. Field B2 can
mean that the Trojan deletes or modifies files without the user's
knowledge. If this has no deeper purpose than the damage, it is
already an attack on field B3, ie sabotage; however, data is changed
to thereby have a purpose such as e.g. the content manipulation,
tracked, then it is an attack on field B2.
The most difficult
fields to defend are those of column "C", since the attack
is independent of the outside, ie the network, and therefore can not
be detected in the network.
Examples of "C" attacks:
Program built into the BIOS of the computer motherboard, which reads
keystrokes and sends them directly over the network to the Internet
to a given server where the data is collected. Also, a reinstallation
of the operating system can do nothing here, since the BIOS of it is
not affected. Likewise, malicious software for espionage,
manipulation or sabotage can be installed in every operating system.
Application programs often contain already
such malicious software or Trojans.
To guard against attacks on
the "C" column, it helps to use only trusted, tested HW and
SW, with Open HW and Open SW, programs compiled from the sources, and
testing the computer if
it is sending
out data even
without any user
intervention.
Unknown networks also include unknown protocols that are not desired by the user, even if these unknown protocols are operated on a known physical network. Thus, at Layer 1, data can be transmitted practically in addition to the usual protocols, without, e.g. a FW knows something about it. Such layer-1 attacks correspond to "under-flying the radar" of the FWs.
The
ACE
An ACE now
physically enables the full protection of networked computers from
espionage, data manipulation and sabotage, which is initiated and
carried out over the Internet.
By asymmetry alone, however, one
would still have no protection against already built in HW and SW
attacks, so in the BIOS, the operating system or applications built
with
malicious
software of any kind.
Against this very difficult to combat type
of attacks on computer systems, networked or
isolated, even today already,
the
review of the program sources, open source, open hardware, programs
compiled from the sources and testing
of the systems if they send something, although the user has not
caused this and did not want. Contracts with the manufacturers, which
state that there are no undocumented functions in HW / SW (contract
penalties),
can also help here. The monitoring of the transport and logistics
routes is particularly important here in order to prevent
manipulation of the HW and SW.
The technical safety of an
ACE against hacker attacks via known networks is permanent.
This protection is also independent of virus definitions,
signatures for network attacks as in IDS / IPS systems usual etc.
The
only prerequisite is that the attacker can not bypass or brake
the
asymmetry.
Now,
the simple explanation why an ACE is physically secured
against espionage via the network and why
this
protection can not be circumvented by the attacker sitting
somewhere on the Internet: the ACE has like said a separate
computer physically only for sending to the Internet and another,
separate from the former, only for receiving from the Internet.
The
sender can then send to the Internet, but receive nothing from the
Internet; therefore, it can not
receive espionage attacks (or other attacks) from the Internet that
can e.g. cause it to broadcast data into
the Internet.
The same applies to data manipulation and sabotage attacks
initiated over the Internet.
The receiver, on the other hand,
can still receive spyware while surfing,
but it
can not send the collected data, such as passwords, texts,
etc., back to the Internet!
The physically secure separation
of the transmitter from the receiver is thus the method for
complete espionage security, as for such espionage attacks that are
both initiated and carried out over the Internet, which probably
affects most of today's Internet espionage and data espionage
(so-called hacking), Industrial espionage, and also spying on
individuals and decision makers.
A
conventional communication endpoint ("red") communicates
symmetrically as regards to
communication
in the network: a single PC e.g. can both receive from the Internet
and send to the Internet. Thus, the end of the data circuit
(transmitter to receiver and also back to the sender) already takes
place at the application level, layer 7 in the ISO / OSI model. (The
ISO-OSI model was established by the ITU in 1983 and co-developed by
the ISO in 1984.)
An application can therefore send and receive
data without user interaction and thus without any user knowledge.
The browser may retrieve data about the user and user-created data,
e.g. via the HTTP protocol to the Internet (passwords, etc.).
Likewise, in principle, all other programs can run on the same
PC. The user or user who runs the applications can not prevent this,
firewalls (FWs) only stop what externally arbitrarily requires access
to the inside (PC), but not what goes from inside to outside.
From
where should the FW also know, so can decide which transmissions from
inside are "good" or "desirable" and which are
not?
Also,
a query to the user whether an application is allowed to send is not
practical, because how often does the user have to do this? And how
should the user always know what the application xyz
is about to send and where to go? And whether this is justified or
not?
Also, this "protection" can be easily circumvented
by smuggling not only the desired data but also others without user
knowledge.
The cause of this dilemma is that the "circuit
of data streams" (analogous to electronics), can be closed,
even below the user level, namely on layer 7, as in a server, where
it is clear that the answers of the server requests
must be automated and immediate, for performance reasons alone and
without human intervention.
But with clients? That shall be
served only by humans? Here you can and should leave the user in
control of when and if the data circuit is closed and for what
purpose.
An important aspect of ACE's is their
invisibility in the network: Since the recipient can not send, an
attacker can also get no feedback from this. So he never
responds to a ping from the outside.
The transmitter is then no
longer accessible via the network, so no longer forced from the
outside to do something undesirable.
An ACE
is therefore not be remotely controllable, at least not without
deliberate users intervention and knowledge.
Indirect protection against DDoS attacks:
Since
an ACE can not be
remotely controlled, it is also the best remedy against DDoS
attacks - distributed sabotage attacks that simultaneously persuade
many once acquired computers to send massive requests to specific
server addresses to bring down the servers or clients - assuming all
users are only using ACE's as devices for Internet use.
Standing
on two legs
As
described above, the ACE has a clear separation between
user-generated and other-person data. The self-generated data must
be created on green, in order to be able to send them. If all users
only used ACE's, all data would at least be on a green device
(somewhere in the network) and would thus be globally protected
against hackers, ie against all network-initiated attacks. Thus, this
data can always be recovered, namely from its original on one of
the “greens”
(senders) of the
creator of the data. This would prevent the mixing of self-created
data (own copyright) and data created by other users (third-party
copyright). Therefore, the ACE
also allowed better protection of data from copyright abuse. An
example of this is the use of email with ACE's, whereby the
forwarding of emails is prevented and can only be done
indirectly via the original sender (enforce a point to multipoint
distribution of data, instead of the usual point to multipoint to
multipoint distribution).
Contrary to symmetrical "end
points" (SCE's) in
the net one stands with the ACE
on two legs and not only on one. Of course, this separation between
data source and sink has consequences for working with
computers.
Further consequences of the asymmetry for dealing with computers and examples
A
consequence of working with ACE's would be that the cooperation via
email and with server-side programs would have to be somewhat
different than with SCE's. E-mails can not be forwarded in an ACE,
as in an SCE, data must never be able to reach the sender from the
receiver, neither over the network nor manually. An email, which one
would have received, should therefore not simply be transmitted from
the receiver to the transmitter and sent from there to other
participants in the email traffic. However, it would be easy to send
the sender an email requesting that the same email be sent to other
recipients. This would also have the privacy advantage that the
copyright must be respected, as the original sender of an e-mail has
control over who gets sent their email.
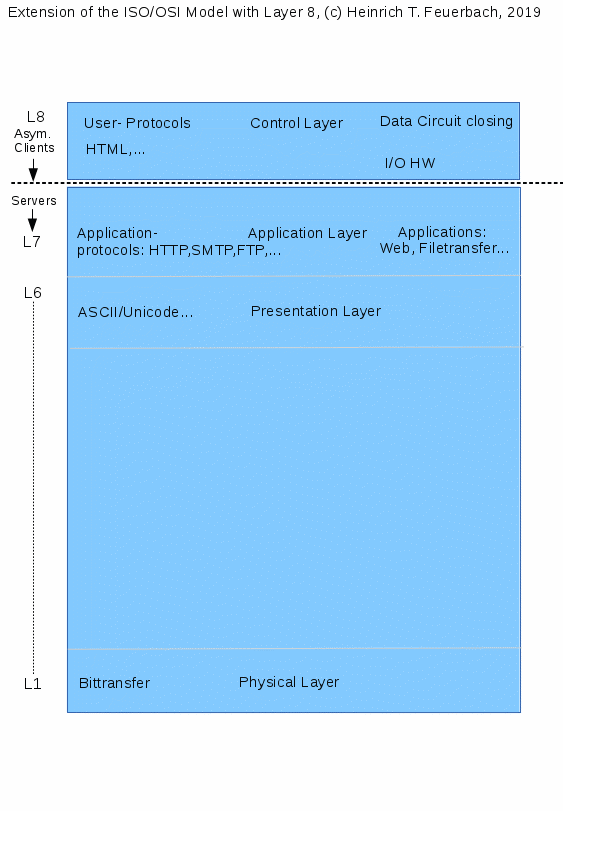
The ACE adds layer 8 to the ISO / OSI layer model
The
well-known ISO / OSI layer model of seven-layer network communication
is extended to eight layers using the ACE, as an ACE
represents a Layer 8 device, cf. Fig.2.
The term "Layer 7
device" or "Layer 3 device" for a network device
results from the lowest level or layer according to ISO-OSI model, on
which the data circuit is closed for the first time. Looking at the
ISO OSI model from level 1 up and looking at which of the levels the
data circuit is closing for the first time, this is the level that
gives the device the "layer x" label. A router e.g. closes
the data circuit at level or layer 3, so it is a Layer 3 device. A
repeater, on the other hand, is a Layer 1 device because it carries
out signal amplification, ie it remains at the purely physical
level.
The user himself exercises control over the
termination of the data circuit at the ACE, thus making the user the
topmost layer on which the data circuit can be closed for the first
time. Of course, in a conventional "client" computer, a
SCE, the mouse, keyboard, etc. are also used by the user, and the
operations in the protocol stack as described above are the same as
they would be in an ACE, but the SCE can easily already have the data
circuit close on layer 7, so act like a server. To put it bluntly, an
SCE is therefore only a server used as a client.
So an SCE is not
a real "endpoint" in a network, just a passing point. That
makes him so insecure. Layer 8 is absolutely necessary for the
description of ACEs or for the assignment of ACEs in the ISO-OSI
model, since the data circuit can only be closed by the user.
The
following is the proposal for a graphical representation of an
ISO-OSI layer model extended by Layer 8:
The ACE also offers effective protection against ransomware
Another important consequence of the asymmetry in the ACE is that of "double data storage". Here I differentiate between users own data and external data. Own data are all from the user of the ACE itself created data using a keyboard. External data are all data the user received by other authors on the receiver-side via the network. Since in the ACE all proprietary data are now entered simultaneously in the sender and receiver using a special keyboard (see the description of a laboratory model below), the users own data is therefore always available on both sides, sender and receiver. This double data storage allows the recipient to be quickly brought back to the previous status after a malware attack. To do this, the receiver is then set up with an operating system image coming from the sender and after restarting, the proprietary data is then copied from the sender to the receiver via the synchronous connection so that both the sender and the receiver have the same status of the (own) data. This recovery method also has great advantages over backups: Since backups of conventionally symmetrically communicating computers are "in series", that is, connected in series (data source to computer to backup), the backup can also be infected by the same malware and thus possibly be unusable. Malicious software often has a "time bomb effect", in which there is a time delay before the malware is activated, so that all backup generations are infected before the user is even aware of the attack. Another disadvantage of backups is that they are never up-to-date, but always (due to the serial arrangement) contain older data than the one the user is currently working on. An ACE, however, works in parallel on two computers. The duplicate data in the ACE are therefore always up to date. If the user now finds that he has been the victim of a "ransomware" attack, all he has to do is to set up the receiver with an image and then copy the user data from the sender to the receiver (via the synchronous connection). Now there is also third-party data, that is, data that comes from other authors than the user and that has been obtained via the network such as the Internet and that "accumulates" over time in the receiver of the ACE. In order to be able to restore it as well after the receiver has been set up with an OS-image, the proxy data is also saved locally on the red device (Balun). From there this foreign data can also be restored via the ring connection from the Balun to the receiver. The receiver is then in the same state as it was before the attack with ransomware and also free of malware from the network. Provided that the ransomware is not copied from the Balun (red) to the recipient; So you have to look carefully at which external data is copied back to the recipient. In order to be able to detect file manipulations as early as possible (not just ransomware) and to be able to replace manipulated files with the originals, I recommend intensive use of asymmetric cryptography: If all users electronically sign their files before sending them, Application programs can use the signature to check all files before opening them, identify tampering and prevent damage. By the way, websites can also be signed by the author before publication, so that browsers can then apply this signature to the websites and can warn the user in the event of manipulations (such as changing links on the page) or, better still, not even load the page. Unfortunately, these simple protection options are currently used only to a very limited extent. The combination of asymmetric cryptography (ACR) and asymmetric endpoints (ACE) also has the decisive advantage that both methods mutually remedy their respective weaknesses: The weakness of the ACR was previously that with symmetrical communicating computers (SCE's) that the signing and encryption process can be viewed or manipulated via the network. This can no longer happen with the ACE: the signing and encryption process on the sender is protected against all external access. Conversely, the ACR protects the weak side of the ACE: the receiver. The receiver is exposed to write and sabotage attacks, albeit significantly less than with a SCE, so the receiver is only "semi-private". If, as mentioned above, all files are protected on the sender with electronic signatures before being sent, such write attacks are no longer possible or at least not unnoticed. The ACR mainly protects the moving data and makes the "data movements" private. The ACE protects the data at rest and also makes the computers private.Important information on the use of the files of the tarball below for ACE V.0.1, laboratory model, the programs and hardware derived from it, as well as all information available here on this page (these instructions have priority over those in the tarball):
License and terms of use:
Attention: the German-language website always takes precedence over the information on my translated websites. This applies in particular to all license terms. The current German website firewalls.feuerbach.info also has priority over information in any of the files that I offer for download.
AKE_PoC.tar.gz
MD5: d66882d464d6a2c523d8c45c4b948343, SHA256: 3c2e1f9f30ed78f031976d1c8d2d2dd0a3d9dd2a104241ed812957ba929a0da1
File size: 7889043 Bytes
AKE_PoC.tar.gz.sig
Fingerprint of Certificate: 92FA6FA30EF95B03346F57D8F4E66A3232C81156
32C81156.asc
Certificate.
Author: Heinrich T. Feuerbach, February 2019